Easily monitor email domains to help prevent BEC attacks
BUSINESS EMAIL COMPROMISE ATTACK (BEC) PROTECTION
Choose Your Email Scanning Plan
SpamExperts Incoming Filtering software offers full inbox protection against spam, viruses and malware with the help of advanced algorithms and spam pattern detection methods.
SCANNING
Outgoing Email Filtering prevents IPs from getting blacklisted as the result of spam unknowingly being sent out through a compromised account, offering full network protection and IP reputation.
SpamExperts Incoming Filtering and Email Archiving bundle offers full inbox protection against spam, viruses, malware, and bulk storage licenses or archiving units based on storage (GB) requirements, to securely archive email for backup and compliance purposes.
SpamExperts Outgoing Filtering and Email Archiving bundle prevent IPs from getting blacklisted offering full network, IP reputation protection, and bulk storage licenses or archiving units based on storage (GB) requirements, to securely archive email for backup and compliance purposes.
SpamExperts Incoming and Outgoing Filtering offers full inbox protection against spam, viruses and malware and prevents IPs from getting blacklisted offering full network and IP reputation protection.
The complete suite of email security offering Incoming and Outgoing full inbox protection, along with Archiving to ensure you never lose another email. Get the highest level of network and IP reputation protection and assured integrity and continuity for emails.
Gain hands-free business email compromise attack protection
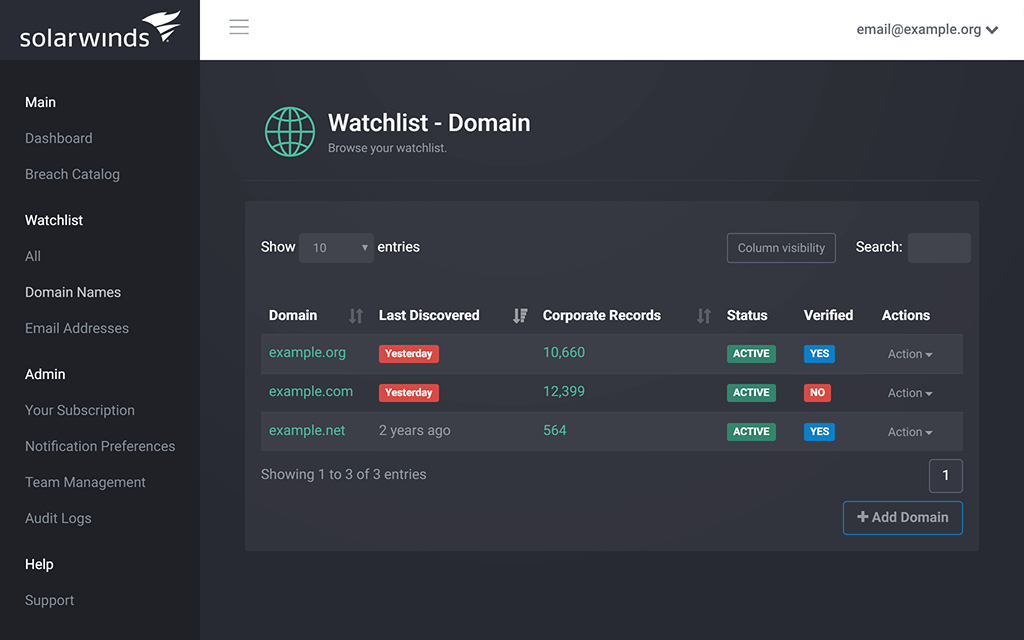
SolarWinds® Identity Monitor is designed to offer straightforward protection for your business credentials and accounts. Identity Monitor experts scan the internet, including the dark web, to discover data breaches and determine whether they contain your company information. Get notified about compromised credentials or email domain infiltration, which can help you know about potential business email compromise (BEC) scams and other types of phishing and hacking attempts earlier.
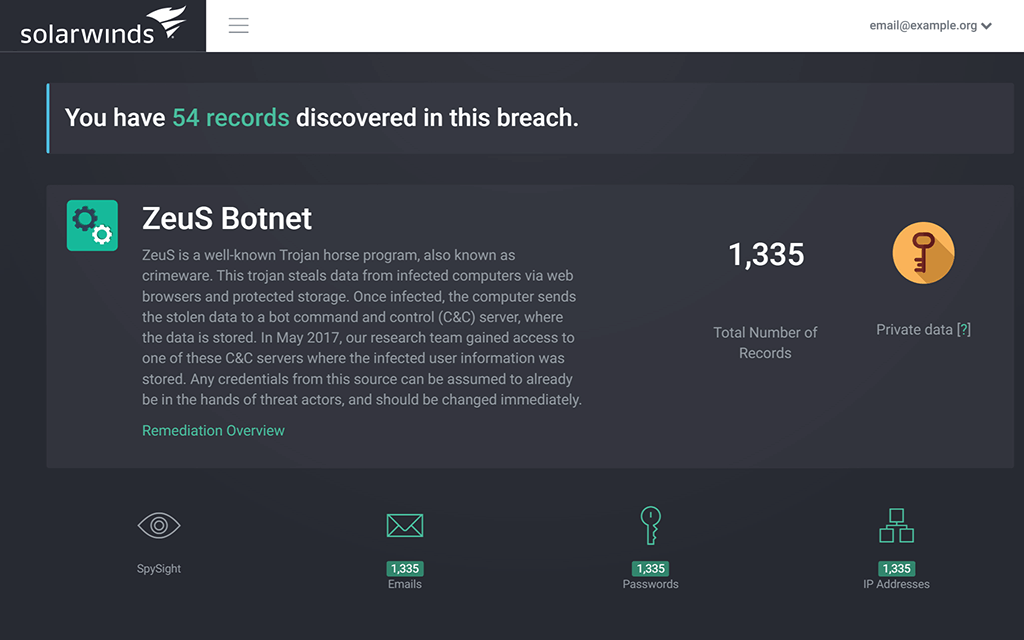
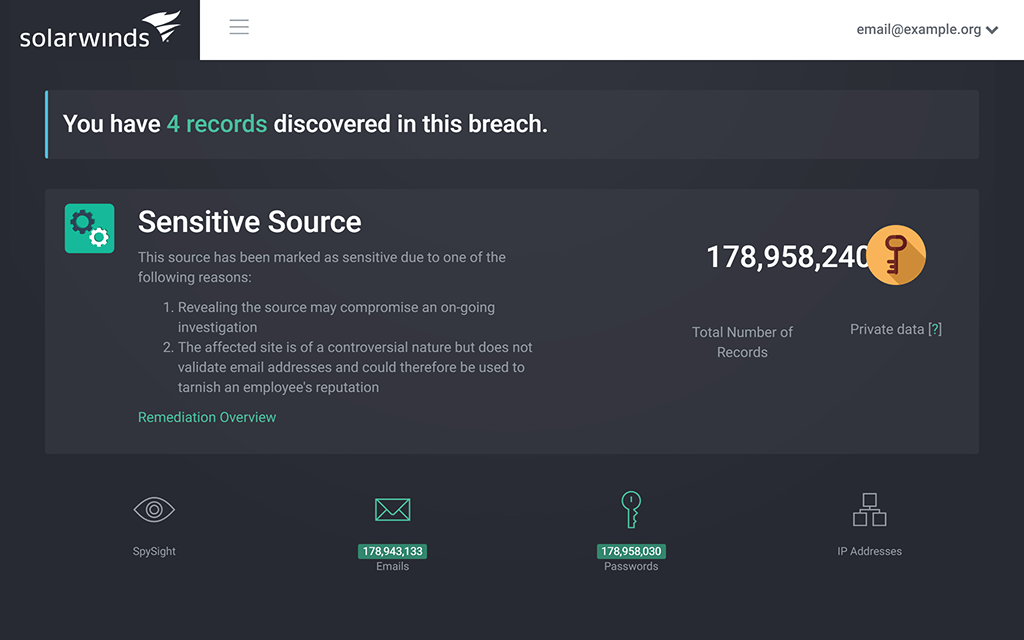
Help ensure extra protection for high-profile accounts
Business email compromise (BEC) attacks often target high-profile accounts, like those belonging to CEOs, board members, or other upper-level management. By infiltrating and leveraging these accounts, hackers can more effectively use social engineering to pressure other employees into complying with their requests. Identity Monitor helps stop this process by offering full monitoring for both work and private email accounts of key employees.
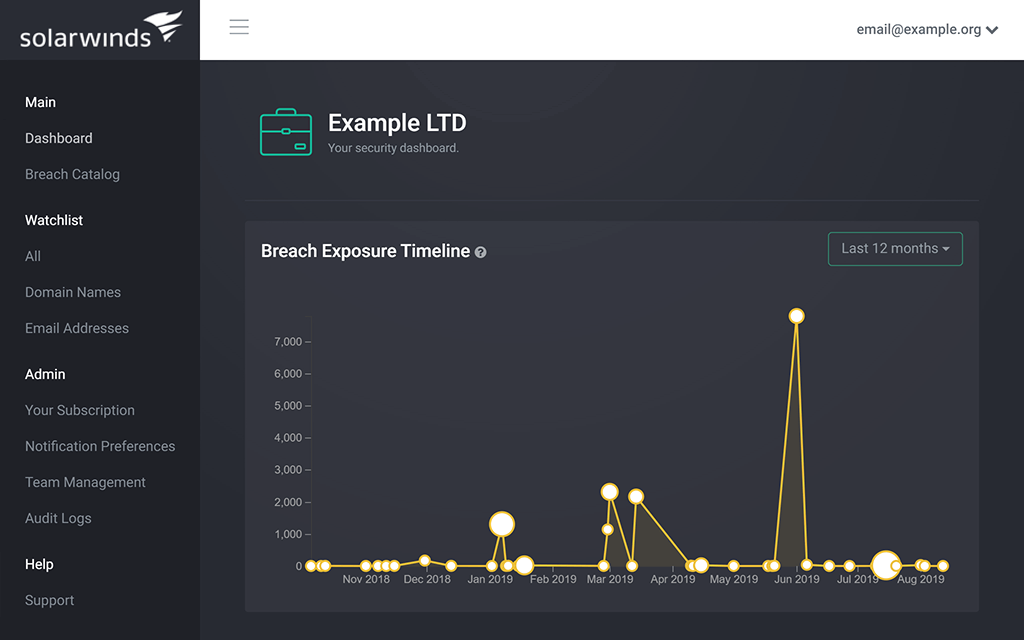
Receive speedy alerts to help prevent BEC attacks
In the case of a data breach, being able to act as soon as possible can make the difference for heading off a business email compromise attack. Identity Monitor is built to send notifications as soon as a breach is identified. In addition, Identity Monitor notifications include context surrounding the breach and remediation advice, so you can more effectively act and shut down accounts or change passwords as needed.
Business email compromise (BEC) occurs when a hacker obtains and leverages company knowledge to manipulate employees into sending funds or sensitive data. This is a form of phishing, which describes various types of cyberattacks, typically performed over email, that trick users into compromising their security. A common first step in an email account compromise attack involves the hacker researching the company. They may scan the website, press releases, social media, and hiring ads. Or they may use phishing emails to obtain access to a company account, where they can secretly view company information, figure out the billing systems, and plan a highly targeted attack. With this information, the hacker can more effectively choose a target and manipulate them into sharing data, such as personal employee information or tax statements, or sending money over a wire transfer. Typically, the hacker impersonates an executive, manager, or even an attorney, which is why BEC attacks can also be considered CEO fraud attacks. The attacker may infiltrate real business email accounts, or spoof accounts by using email addresses close to the real account. The attacker then may use the principles of social engineering to pressure a lower-level employee or customer. They may leverage corporate standing, use terms like “urgent,” or send the message toward the end of the workday. On the other hand, executives can also be a likely target, as they have access to especially valuable information. The finance and legal departments may also be subject to a targeted attack. Unfortunately, once data is shared or wire transfers go through, it may be impossible to reverse the damage.
Unfortunately, it can be difficult to recognize and stop a corporate email compromise attack while it’s happening, or even after the fact. Attackers thoroughly prep for their attacks, which means their messages often include references to company information, executive names, or internal funding plans that may initially make the email look authentic. However, employees can be on the lookout for unusual messages from executives, and always take extra steps, like calling the real team member directly, to ensure requests for sensitive data or wire transfers are legitimate. Any email demanding “urgent” action may be suspicious. In addition, employees must look twice at sender emails, as they may appear legitimate but are likely slightly incorrect, with errant letters, numbers, or punctuation. The best way to avoid an email compromise attack is to take steps to prevent email compromise in the first place. Companies must keep a close watch on business accounts and credentials. With the right monitoring software, you can receive alerts as soon as a breach is detected, so you can reset passwords and take other steps to help ensure security.
Business email compromise protection is critical for any business hoping to avoid the loss of funds or sensitive data. The FBI’s 2019 Internet Crime Report cited 23,775 complaints regarding BEC, with a total of $1.7 billion in losses for the year. Protection against BEC fraud is important for both small and large companies. Small companies may not have strict data protection measures or email security training, if they assume they’re not a target. Large companies may be vulnerable due to a complex company structure that may leave more opportunities for hackers to exploit. BEC scams are a threat regardless of industry type. To help ensure protection against BEC scams, it’s important to have an up-to-date approach to security. BEC attackers can be highly creative in how they target companies, and last year’s strategies may not be the same as those popular this year. For instance, the FBI report noted an increase in BEC complaints related to payroll funds, where hackers send HR an email as an employee, with a fraudulent direct deposit update. Companies must remain vigilant and take proactive protection measures whenever possible.
Business email account compromise protection requires a multi-pronged approach to preventing, recognizing, and quickly addressing security threats. To combat the social engineering aspect of corporate email compromise, companies should consider an email security awareness program for employees. They should train staff in how to recognize a range of suspicious requests, and mandate they never reply directly to risky emails. They should instruct employees to always cross-reference a sender’s email and preferably contact them over the phone to ensure the request is legitimate. In addition, businesses should warn employees not to post potentially compromising information on social media or business sites. Businesses can also establish a company domain name for their email, with official accounts, rather than rely on free services that may be easier to hack. They can set up email filters for words like “payment” or “urgent” that will flag these emails as potentially risky. Companies can also invest in more sophisticated tech solutions, as employees are unlikely to catch suspicious emails in every scenario. Monitoring tools help with business email compromise protection by continually tracking corporate email domains and credentials. These tools can scan many potential places where these compromised accounts may show up, including the dark web. If tracked credentials are found, the monitoring software will automatically send an alert, so the company can quickly act and help prevent security breaches.
SolarWinds Identity Monitor is an automated monitoring SaaS solution designed to scan data breaches, discover compromised accounts, and give companies the information they need to quickly act on threats. This solution is built to provide the insight you need to identify and head off BEC attacks. Identity Monitor is supported by a team of researchers who scan data leaks, including those on the dark web, and process the data to discover whether a company’s credentials or other monitored information is part of a breach. If a breach occurs, it’s critical to examine recent account usage and reset passwords in case a BEC hacker has already put the information to use. Identity Monitor includes an extra focus on key employees, like executives or board members, allowing companies to monitor both their work and private email address. Corporate email compromise attacks often leverage these key accounts. If an exposure does occur, reaction time is critical. Identity Monitor is designed to immediately notify you when it discovers monitored accounts or credentials. That way, you can reset passwords or address potential security issues as quickly as possible. These alerts include severity level and contextual information, so you can take appropriate action with confidence. As relevant, Identity Monitor is designed to specify display password encryption type, account signup time, and personally identifiable information. If you’re curious whether your corporate credentials are currently at risk, you can enter your email for insight.
Other SolarWinds Solutions to Help Prevent Data Breaches:
SolarWinds Security Event Manager
SolarWinds Patch Manager
SolarWinds Access Rights Monitor
Related Features:
Account Takeover Prevention
Private Email Monitoring
Monitor Multiple Domains
Credential Exposure Notifications
Data Loss Prevention
